Is your Slack workspace secure?
Slack and other cloud-based collaboration tools make getting work done faster, more efficient, and often more enjoyable; however, new and revolutionary ways of working also require new considerations for both conduct and security.
Whether it’s sensitive operational data of your own, or the sensitive data entrusted to you by customers, your organization is its steward.
There have always been (and there will always be) bad actors looking to take advantage of weak points in an organization’s security infrastructure. As communication and collaboration infrastructure evolves, so do their tactics.
The same is true for accidental breaches. There will always be that colleague who consistently responds to phishing emails, clicks questionable links, keeps passwords written down on their desk, and sends work emails from their personal account. They’re the same colleagues who routinely go rogue and install unvetted, broadly-scoped apps from outside the Slack Marketplace (formerly App Directory) to your workspace without checking in.
IT managers and security-minded Slack admins alike have voiced their anxiety around security -- not because Slack is inherently insecure, but because it’s another set of tools for both bad actors and well-meaning employees to cause a security incident.
Need a quick way to break down and share key information on Slack security with your team in a simple (and fun*) format? Try these slides!
Why is Slack security so important?
1. Slack (and most cloud providers) operate on a shared responsibility model.
What does that mean? Shared responsibility means that while Slack does take security very seriously and continues to invest significant resources into its security infrastructure, it must also open at least some channels in order to provide the functionality we love and rely on. Opening those channels means removing at least some security barriers, so there’s an expectation that your organization must take some responsibility for its own security.
This arrangement is nothing new, and certainly not exclusive to Slack.
Many SaaS tools, services, and platforms operate on this principle because it’s impossible to anticipate, much less protect against every potential user action that might adversely impact security. While it would be possible to create a more secure system by eliminating all entry points, that system would have limited (if any) value to users.
In summary, as much as it is Slack’s responsibility to keep its security infrastructure fortified to the greatest extent possible, it needs to open some gates in order to serve its users, so there’s a crucial responsibility on you and your team to maintain solid security standards as well.
2. Research found 18.1 percent of all documents uploaded to cloud-based file sharing collaboration services contained sensitive data.
Take a moment to let that sink in. Roughly one out of every five documents dragged into your collective Slack channels could very well be sensitive data that should be protected.
This doesn’t mean sensitive documents shouldn’t live in Slack (or other SaaS services) - but it is on you and your team to be good shepherds of that data when you do bring it in.
It’s important to remember that because we do so much in Slack that there’s bound to be a ton of data in there -- and according to the study referenced above, much of it is likely to be sensitive in some way or another.
3. Insider threats are responsible for a considerable number of data breaches.
Likely many more than you expect -- according to some research insider threats account for as much as 43 percent of breaches. We often think of security vulnerabilities in terms of protection against outside attacks, but in truth, it’s nearly as likely that a security leak originates from within your own organization.
This can be a result of malicious action, but once again, the 'most likely’ scenario in our minds isn’t always the most common one. Accidental breaches are nearly as common or perhaps more common than deliberate breaches. Your security strategy should protect against accidental actions by well-meaning actors just as it should protect against malicious actions.
4. Compliance requirements (e.g. FINRA, HIPAA, GDPR) raise the stakes and the level of complication for data handling and security even greater.
Slack can be configured for HIPAA, FINRA, and other data regulations, but once again even the most secure system is only as secure as its operators. How you handle that information within any system is a critical element of its security.
Slack invested a great deal of its resources into building the tools you need to ensure your workspace is as insulated as possible against security threats, but it’s just as important to educate employees on how to manage data and security properly and reinforce the importance of good data stewardship.
At Polly, we also invest heavily in security and believe in its vital importance. Because of that, we put together this Slack security guide to help you and your colleagues keep your data safe, whether you’re a small team using the free plan or a large organization using Enterprise Grid, or somewhere in-between.
IMPORTANT NOTE: No system is perfectly secure. While our goal is to provide as much information as possible, this guide is not an exhaustive list of security actions to take. It is for informational purposes only and is in no way a substitute for your own due diligence or professional advice and assistance.
This guide is simply a conveniently compiled list of useful tips to improve your Slack security framework. It’s still absolutely imperative for you to assume responsibility for your organization’s cloud security and your own continued security education.
The Fundamentals
Effective security is layered, like an onion. Peel back one layer, and all you see underneath is more onion. Defeat one layer of security, and you’re just presented with another layer.
You could consider these first few security measures we discuss the core of that onion. It’s a great place to start.
Most of these measures don’t require any expensive or complicated tools, developer resources, or managed services, yet they’re an important fundamental layer of protection.
Despite their relative simplicity and negligible cost, many organizations still operate without them in place. But not you, right? You’re running a secure operation.
Basic Access Controls
(Available in all plans)
There are a number of security features Slack offers at every service level. They’re a great place to start because you don’t need any specialized tools, knowledge, or account features.
App Installation
One of the greatest benefits of Slack is its ability to integrate all types of third-party tools into your daily workflows. It offers several features that provide control over which apps, and which types of tools can be installed.
Restricting installations to Slack App Directory:
One of the simplest and lowest-friction ways to protect your workspace from rogue app installs is to limit app installations to those from the official Slack App Directory. Slack reviews every app in the directory before making it available to the public.
This doesn’t mean there aren’t any apps in the directory that might be problematic for your organization from a privacy/security perspective--that’s going to be different for everyone--but it does help mitigate the risk of truly questionable apps making it onto your workspace under the radar.
Pre-approval list
To take it a step further, you can whitelist (define a list of pre-approved) apps users in your Slack workspace can install.
Manual app approvals
This method requires more administrative overhead, but does offer even greater visibility and control over the apps in your workspace. Users will need to request admin approval for any app they wish to install.
User management
User and access management are crucial to security. Slack offers several options to make it simple to manage access to your workspace, and individual areas within that workspace.
Manual, but expedient user management
If you don’t have an automated user management tool in place (many smaller orgs don’t), it’s vital to have an offboarding checklist to help ensure there aren’t any users with access to data they shouldn’t have.
Guest users vs. full users
If you need to bring someone from outside your organization into Slack so they can communicate with your team, you can add them as a guest user and manage which channels they have visibility and access to.
Channel privacy
There are some conversations and pieces of data that might be sensitive, even internally. In this case, you can create private Slack channels that are only available to individual invitees.
Bot/App Scopes
App/Bot scopes determine the level of access a third-party application has to the data within your Slack workspace. If you’ve ever installed a Slack app or bot, this page probably looks familiar:
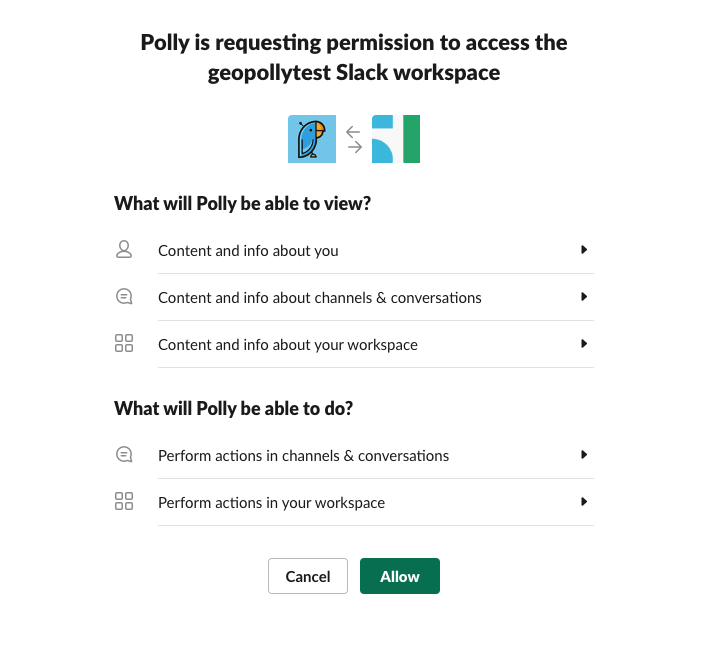
Every app and bot in the Slack ecosystem has a scope of access that is granted on installation.
Historically, many cases existed where apps and bots were required to select their required scope from a relatively short list of access levels. This caused issues for many developers (including Polly!) because it forced them to request a greater scope of access than they actually needed.
Slack listened to customer and developer feedback on this topic and deployed a solution. During the 2019 Spec Developer Conference, Slack released a more granular set of scopes that application developers could use in order to request an appropriately limited amount of access in order to provide their service, and nothing more.
Our CTO, Bilal Aijazi spoke on this topic during the opening keynote at Spec. You can catch his talk and others on this topic below:
Force Two-Factor Authentication (2FA)
(Available in all plans)
Two-factor authentication is one of the quickest, easiest, and most accessible way of increasing account security without adding any extra hurdles. As a workspace administrator, you can require all users in your workspace to set up 2FA.
While 2FA is a significant step toward greater security, there are still varying levels of effectiveness, based on the 2FA format you choose.
Email (a limited-time single use code sent as a text to you in an email)
Email-based 2FA is generally considered the weakest format, because once your email account is compromised, your second authentication factor is also compromised. There’s no requirement for the attacker to have a specific device or be in a particular place. Once someone controls your email account, they can receive your email-based 2FA codes from nearly anywhere. Note: Slack does not offer this less secure method as an option when setting up 2FA.
SMS (a limited-time single use code sent to your device as an SMS text message)
SMS-based 2FA is generally considered a more secure option than email, but it’s not infallible.
Your mobile carrier can transfer your phone number to another SIM instantaneously without physical access to either device. This does happen in the wild, and it’s usually the result of a social engineering attack (when an attacker manipulates humans to give up protected information or access).
In addition to the SIM-jacking vulnerability above, an SMS can simply be sent to multiple devices at once, if the user has multiple devices signed into the same OS account. If someone gains access to one of your mobile devices and your lock screen privacy settings allow messages to be read without authenticating, they can potentially intercept your SMS 2FA codes by reading them as they appear on the lock screen.
App-based 2FA (a limited time single-use code generated by an authenticator app):
If you’ve ever felt the pain of losing a device with your 2FA codes in it, you already know that in order to defeat app-based 2FA, an attacker would have to have the specific mobile device in hand (not just the sim associated with the user’s phone number).
Of the three most common methods, app-based 2FA is generally considered more secure because it is locked down to a single device, but there are still more secure authentication methods available.
Hardware Keys (a small physical device that generates authentication codes)
Physical hardware keys like a Yubico’s Yubikey offer what is considered to be an even greater level of security than app-based 2FA, though the list of services that accept hardware keys as an authentication method is much smaller than those who accept the other methods above.
ADVANCED
SAML/SSO
(Available in Plus and Enterprise Grid)
Single Sign On (SSO) providers like Okta make it possible for employees to log into apps and services without managing individual account login credentials. By eliminating individual account credentials you’re eliminating a vast number of potential attack vectors.
Slack offers SSO integration functionality at the Plus and Enterprise Grid level.
Automated User Management (provisioning/deprovisioning via SCIM)
(Available in Free, Standard, Plus, and Enterprise Grid)
Automated user management makes it simple to provision and deprovision user accounts automatically. For example, if an employee is marked as ‘terminated’ or moved to a different department in your HRIS, their requisite accounts will be de-provisioned across all the applications they had access to (or provisioned, in the case of a departmental transfer or promotion).
In many cases, SSO providers also handle automated user management.
Without automated user management, it’s surprisingly common for users to retain access to a live user account despite no longer being a member of an organization. Even if you don’t have automated user management, make sure you have an offboarding checklist that ensures departing users' access to critical systems is revoked.
Domain Whitelisting
(Available in Plus and Enterprise Grid)
At its most simple, Domain whitelisting restricts access to your Slack account based on what network the traffic is coming from. This means even if someone has all the correct login credentials, they won’t be able to log in unless they’re coming from one of the networks you’ve whitelisted (for example, from a network at your HQ).
This way, even if every other security protocol is breached, there’s no way to log in and access your data without additional access to your whitelisted networks.
Mobile Password / Biometric ID
(Available in Enterprise Grid)
By enforcing a mobile passcode or biometric ID challenge, even if an employee’s device is stolen, their devices won’t be able to log into your slack account without their individual device passcode, or biometric “key” (most commonly a fingerprint or Face ID).
Block File Downloads and Message Copying
(Available in Enterprise Grid)
Admins of Enterprise Grid accounts can restrict file downloads and message copying capabilities to devices managed by an Enterprise Mobility Management (EMM) provider.
EXPERT
Encryption Key Management (EKM) (API)
(Available in Enterprise Grid)
Encryption Key Management (EKM) allows organizations to shut off access to content unilaterally in an instant. This is particularly useful to organizations in heavily regulated or sensitive industries.
Slack recently introduced EKM capability to Enterprise Grid users.
Audit logs (API)
(Available in Enterprise Grid)
Audit logs make it possible to see who took what actions within a system, where they took those actions from, and when. This information can be incredibly useful in keeping track of potential security issues or looking back in retrospect.
Enterprise Grid users get access to the Audit Logs API, which can be connected in a variety of ways, from specialized third-party tools to custom internal apps.
Session Management (API)
(Available in Enterprise Grid)
Session management allows admins to end the session of any user in their workspace. This is often useful in the case of a device loss, or for any other reason that might require a device to have its access revoked temporarily until the user re-authenticates.
Slack provides session management functionality to Enterprise Grid users through its Session Management API.
THE HUMAN ELEMENT
You can have the most secure system architecture, but all it takes is one malicious or uneducated user to cause a significant incident. Conversely, a well-trained workforce that takes security and privacy seriously is a powerful security asset. That’s why it’s crucial to have policies, procedures, and education in place.
Security Policies
Your security is only as strong as the policies that guide and enforce it. Make your policies clear, present, and non-negotiable.
In addition to this, it’s important to do everything you can to make secure operation as easy and frictionless as possible. The less arduous your security policies feel, the more likely they are to be followed consistently.
Infosec Education / L&D
What’s your plan for continuing education for your team? Policies are worthless if they aren’t understood or followed. Keep your team educated on security, why it matters, and how individual members can play their part.
Education is a journey, not a destination -- make sure to provide refreshers and access to further education for your team so they can play a strong role in keeping your operation secure.
In conclusion
Security is an important factor in determining which systems you use. Slack has a great set of security features and tools that you can leverage to fortify your infrastructure, but it’s just as important to develop a working security plan, solid procedures, and to ensure members of your organization follow them.







/Internal%20Comms%20Fun%204.png)
/Ask%20questions%20fun%204.png)





